Our Managed It Services PDFs
Wiki Article
8 Simple Techniques For It Service Melbourne
Table of ContentsManaged It Services Melbourne Fundamentals ExplainedLittle Known Facts About It Services Melbourne.A Biased View of It Services MelbourneGetting The It Services Melbourne To Work
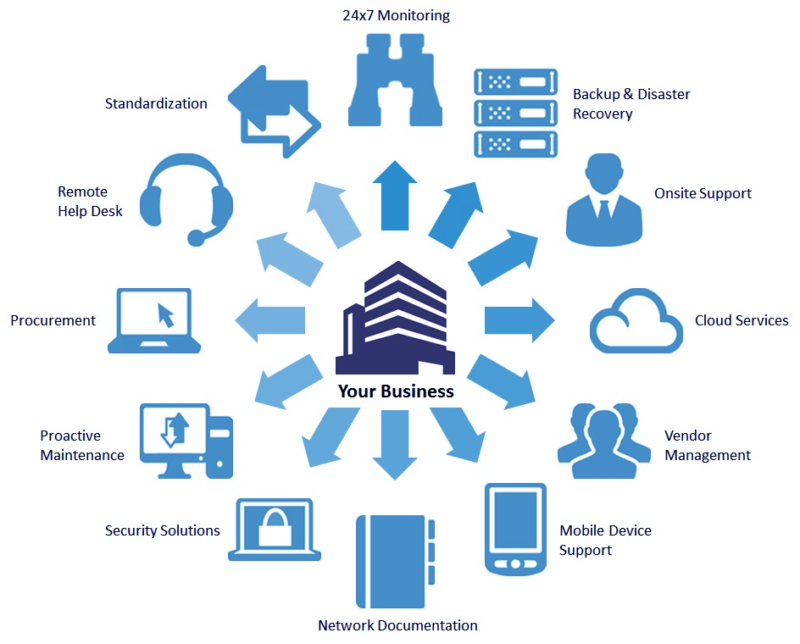
As foresaid, IT support deals end-to-end handled IT services, which consist of these generally: An IT framework has a number of laptop computers, workstations, printers, servers and hardware systems. A small damages or malfunction may end up in a great loss, which can be of crucial data or info. This occurring ultimately influence on the company's returns as well as connection.These plans have multi-factor verification, preventing out of the state logins and many other ones in an excellent duty. This is exceptionally for the companies that allow employees to utilize their own phones for carrying out tasks. This bring-your-own-device (BYOD) is not every typical, yet still exists. The assistance supplying business place their team to secure that information and possessions from hackers or abuse.
It makes certain that just safe and secure tools will certainly be able to do from another location, as they would certainly can protecting the delicate information of the business. It describes the on-demand accessibility of computer system sources, including information storage and also computing power. This taking place does not call for any type of direct energetic management by the user.
As its advantages are incredible, a growing number of business have started changing to the cloud for holding their data. managed it services. For keeping their secret information about customers as well as their customer experience (CX) safe, it includes some exceptional security features. The technology support group manages it well in 2 methods: Guaranteeing configuring and also handling the cloud system for holding a variety of requisite applications, information monitoring, IT sustain and also downtime, Using the total safety and security to what comes under the handled IT solutions from cyber offenders.
The Basic Principles Of Managed It Services For Law Firms

Something failed. Wait a minute and attempt again Try again.
Businesses are significantly moving their IT infrastructures into the cloud (managed it services). Lots of venture companies currently operate in multi-cloud atmospheres or utilize hybrid on-premises as well as cloud-based IT designs. These intricacies require the need for IT sustain solutions to deal with these systems. Cloud computer support is an IT service that aids companies manage their cloud-based framework.
All about It Services Melbourne
Information back-up as well as recuperation assistance include the implementation of information backup remedies, such as cloud-based, disk-based and tape-based backups. Data backup and healing assistance likewise involves screening data recuperation options to guarantee that they are reputable and efficient in the event of a data loss or corruption. IT sustain is crucial for companies that depend heavily on their data, such as those in the medical care and finance sectors - managed it services for law firms.Office innovation changes rapidly and gets a lot more complicated by the year. Whereas the mass of job-related computer once occurred within the workplace walls and inside a secure border, today's dispersed labor force carries out business from houses, cafe, autos actually anywhere with internet access. Supporting and safeguarding the myriad tools and also accessibility factors workers now rely upon to remain efficient has created a great deal more help IT groups that commonly are already spread out too slim.
Organizations resort to managed solutions service providers (MSPs) for a range of reasons, yet most commonly, they are utilized by companies with no internal IT team or those that desire to utilize their internal IT specialists to concentrate on specific initiatives instead than operational duties for managing technology. MSPs give a huge range of services from the fundamentals such as assistance workdesk support and keeping IT tools and also solutions working all the way up to giving the complete collection of IT capacities, including cyber safety, web connectivity, application assistance, data back-ups, and catastrophe recuperation.

It Services Melbourne Fundamentals Explained
Handled go to this web-site IT solutions are far from one-size-fits-all, so partnering with an MSP that recognizes your organization and is proactively invested in helping you fulfill your objectives is crucial.Potential risks outside the network are protected against, guaranteeing that a company's sensitive information continues to be within. Organizations can go even more by defining added interior boundaries within their network, which can provide better safety and also access control. Accessibility control defines individuals or groups and also the gadgets that have access to network applications as well as systems thereby denying unauthorized accessibility, and also possibly risks.
A susceptability is a bent instance in a software program system as well as a make use of is an assault that leverages that susceptability to get control of that system. When a manipulate is introduced, there is usually a home window of chance for assailants to manipulate that vulnerability before the safety spot is used.
Sandboxing is a cybersecurity method where you run code or open data in a safe, separated environment on a host device that mimics end-user operating atmospheres. Sandboxing observes the data or code as they are opened up and searches for destructive Your Domain Name behavior to stop threats from jumping on the network. As an example malware in data such his explanation as PDF, Microsoft Word, Excel and also Power, Point can be safely detected and also obstructed before the documents get to an unsuspecting end customer.
Report this wiki page